Data Working To Uncover Identities Website
Startup Stealth Data Working To Uncover the Identities of Website Users ...
While that's certainly true, it's the info that's available through those sleazy background check websites that makes things even worse. Combine the public info with the private details, it's quite easy to build a profile for someone (or anyone!) with quite accurate details. Then,...
https://www.newsbreak.com/news/2272347260996/startup-stealth-data-working-to-uncover-the-identities-of-website-users
Startup Stealth Data Working To Uncover the Identities of Website Users ...
Stealth Data's third co-founder Chad Sneed experienced marketing frustrations firsthand through his family's dealership, Dennis Sneed Ford in Gower, Missouri. Sneed, who's a vice president and...
https://www.newsbreak.com/news/2271584181064/startup-stealth-data-working-to-uncover-the-identities-of-website-users
Understanding identities in IIS - Internet Information Services
If you create a website, and then point the physical location to C:\inetpub\wwwroot, the following users, and groups are automatically added to the site's access control lists. If you want to disable this feature and manually add accounts to the IIS_IUSRS group, set the manualGroupMembership value to true in the ApplicationHost.config file.
https://docs.microsoft.com/en-us/troubleshoot/developer/webapps/iis/www-authentication-authorization/understanding-identities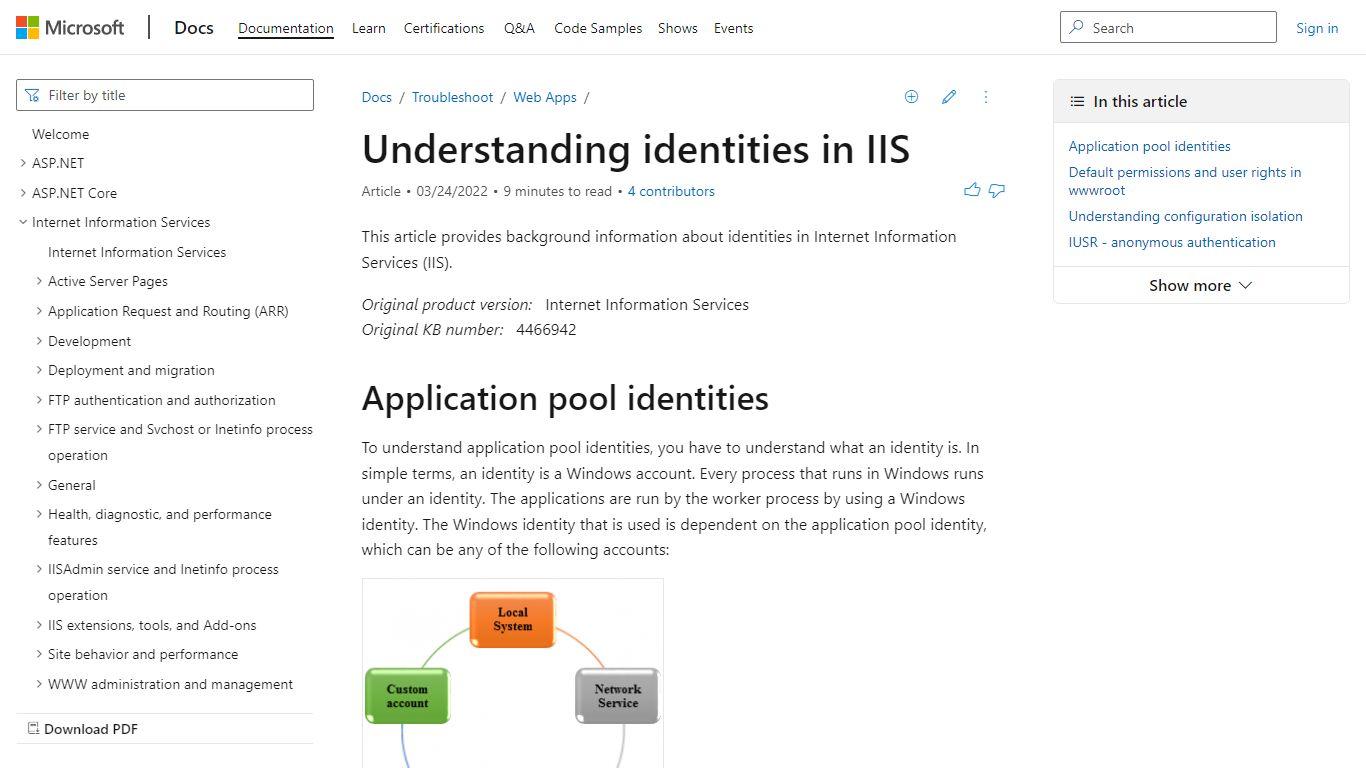
Identity Theft Statistics, Facts and Trends You Need to Know in 2022
Identity fraud caused an economic loss of $16.9 billion 6 in 2019, according to Javelin Strategy and Research. This is despite the fact that the percentage of people who fell victim to identity...
https://www.cloudwards.net/identity-theft-statistics/
Twitter API Abused to Uncover User Identities | Threatpost
Twitter said that malicious actors, with potential ties to state-sponsored groups, were abusing a legitimate function on its platform to unmask the identity of users. The social media giant said ...
https://threatpost.com/twitter-api-abused-to-uncover-identities/152521/
Microsoft Identity Web authentication library overview - Microsoft ...
Microsoft Identity Web is available on NuGet as a set of packages that provide modular functionality based on your app's needs. Use the .NET CLI's dotnet add command or Visual Studio's NuGet Package Manager to install the packages appropriate for your project: Microsoft.Identity.Web - The main package.
https://docs.microsoft.com/en-us/azure/active-directory/develop/microsoft-identity-web
Identity management 101: How digital identity works in 2020
Identity and access management (IAM) is the class of software and services on the computer networks' side of the transaction, dedicated to fulfilling their responsibilities to you in that regard....
https://www.zdnet.com/article/identity-management-101-how-digital-identity-works/
“Anonymized” data really isn’t—and here’s why not
The Massachusetts Group Insurance Commission had a bright idea back in the mid-1990s—it decided to release "anonymized" data on state employees that showed every single hospital visit. The goal was...
https://arstechnica.com/tech-policy/2009/09/your-secrets-live-online-in-databases-of-ruin/
'Anonymous' browsing data can be easily exposed, researchers reveal ...
Eckert, a journalist, paired up with data scientist Andreas Dewes to acquire personal user data and see what they could glean from it. Presenting their findings at the Def Con hacking conference in...
https://www.theguardian.com/technology/2017/aug/01/data-browsing-habits-brokers
Researchers Scan the Web to Uncover Malware Infections - Dark Reading
Dozens of companies and universities regularly scan the Internet to gather data on connected devices, but some firms are looking deeper to uncover the extent of detectable malware infections....
https://www.darkreading.com/security-monitoring/researchers-scan-the-web-to-uncover-malware-infections
Unauthorized Transmission and Use of Personal Data
they use collective data, along with sophisticated statistical analysis techniques and psychological models, to predict peoples' purchasing preferences and behavior and to identify those factors that most strongly influence consumers' loyalty and choices. 6 they then combine this intelligence with detailed information on specific individuals and …
https://www.scu.edu/ethics/focus-areas/internet-ethics/resources/unauthorized-transmission-and-use-of-personal-data/
Managing user identities and secure access at Microsoft
303,000 global identities 488,000 partner identities 10,400 privileged identities that have some level of elevated access 15 million authentication requests per month 1.6 million cloud applications—99 percent of our apps—using Azure Active Directory (Azure AD) 3,000 applications using Active Directory Federation Services (AD FS) Azure AD Connect
https://www.microsoft.com/en-us/insidetrack/managing-user-identities-and-secure-access-at-microsoft